[NEW!] New case infection w/same payload type & infection MO in different domain.
Landing page: 3thtyjtyjcc.ns02.us/closest/209tuj2dsljdglsgjwrigslgkjskga.php
Payload: ZeroAccess
Exploit: Java: #CVE-2010-4476 #CVE-2013-0422, PDF: #CVE-2010-0188, CVE-2009-0927
Sorry for the report in text-->
http://pastebin.com/raw.php?i=HPESHngh
I am on a half way on a plane of a long trip, got many spare time so I checked some queries to malware site. I received the report to investigate a Blackhole Exploit Kit, the clue was the infected domain of 33sdfguuh.mywww.biz, I had no idea so the first try I did was requesting the domain in the urlquery and ending up with the below suspected landing page url:
33sdfguuh.mywww.biz/closest/209tuj2dsljdglsgjwrigslgkjskga.php
Got so attempted so I fetched:
--2013-02-05 21:45:24-- h00p://33sdfguuh.mywww.biz/closest/209tuj2dsljdglsgjwrigslgkjskga.php
Resolving 33sdfguuh.mywww.biz... seconds 0.00, 89.253.232.149
Caching 33sdfguuh.mywww.biz => 89.253.232.149
Connecting to 33sdfguuh.mywww.biz|89.253.232.149|:80... seconds 0.00, connected.
:
"GET /closest/209tuj2dsljdglsgjwrigslgkjskga.php HTTP/1.0"
Referer: http://malwaremustdie.com
"Host: 33sdfguuh.mywww.biz"
:
HTTP request sent, awaiting response...
HTTP/1.1 200 OK
Server: nginx/1.2.6
Date: Tue, 05 Feb 2013 12:45:24 GMT
Content-Type: text/html
Connection: close
X-Powered-By: PHP/5.3.10-1ubuntu3.4
Vary: Accept-Encoding
:
200 OK
Length: unspecified [text/html]
Saving to: "209tuj2dsljdglsgjwrigslgkjskga.php"
"2013-02-05 21:45:27 (90.4 KB/s) - 209tuj2dsljdglsgjwrigslgkjskga.php saved [113594]"
The inside was the common Backhole v2.x's landing Page ofuscation,
which manually cracked to be plugin detect script like this -->>[PASTEBIN]
Some of the highlight are below:
1. The usage of the pair of directories of /closest/ &
2. they don't put shellcode or the malware payload download in the landing page,
instead scattered in the exploit file infector.
3. two pdfs, two jars and one payload.
BHEK is BHEK, by using our guideline -->>[HERE] you can get these samples:
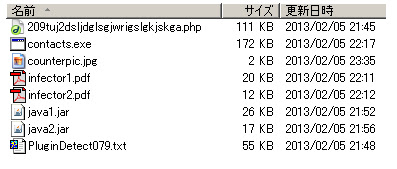 FYI the 2 PDFs urls is are as per below (this is for people who got attack by
these Blackhole which mostly seeing these PDF downloads URL in their log..)
FYI the 2 PDFs urls is are as per below (this is for people who got attack by
these Blackhole which mostly seeing these PDF downloads URL in their log..)
h00p://33sdfguuh.mywww.biz/closest/209tuj2dsljdglsgjwrigslgkjskga.php?dsmq=30:1n:1i:1i:33&lllsxi=3g:3a:3c&bdm=30:33:1n:1m:1h:33:30:1o:30:1h&uzz=1k:1d:1f:1d:1g:1d:1f
h00p://33sdfguuh.mywww.biz/closest/209tuj2dsljdglsgjwrigslgkjskga.php?qbzntsus=30:1n:1i:1i:33&cazv=39&alltb=30:33:1n:1m:1h:33:30:1o:30:1h&mkitrggt=1k:1d:1f:1d:1g:1d:1f
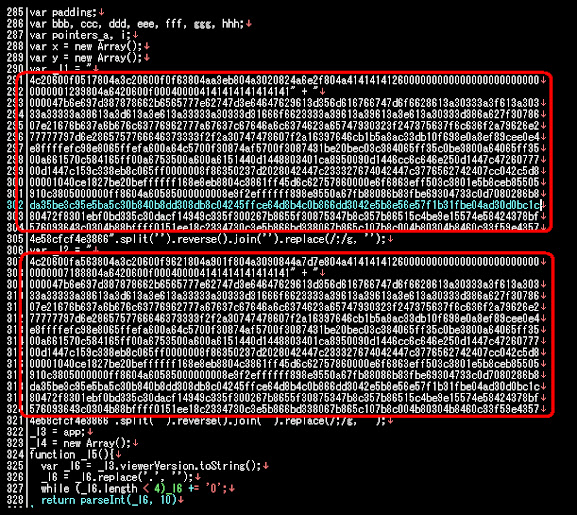
I started to get the payload from the smallest size of PDF, to find the JS/Evil/Code
written in the 0x11AF-0x2768 section with text below:
 The red mark is the evil script, where the purple mark is the long
obfuscation var/array, and the yellow mark is the deobfuscator logic.
Following the usual method to decode this, we'll find the infector script burped
as per first upper part below, marked area is the shellcode in text:
The red mark is the evil script, where the purple mark is the long
obfuscation var/array, and the yellow mark is the deobfuscator logic.
Following the usual method to decode this, we'll find the infector script burped
as per first upper part below, marked area is the shellcode in text:
 And the lower part which having Libtiff overflow CVE-2010-0188 exploit code:
And the lower part which having Libtiff overflow CVE-2010-0188 exploit code:
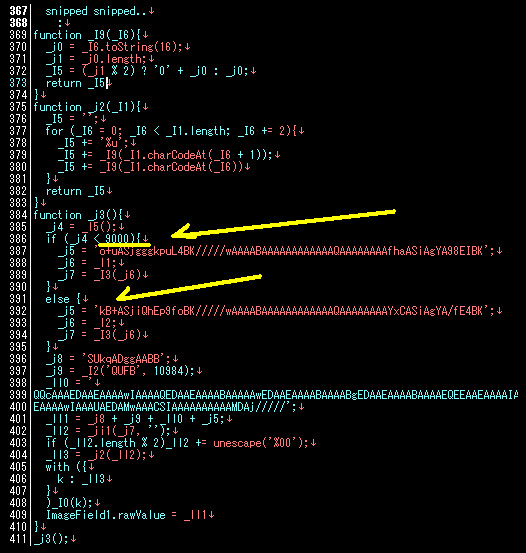 *) Noted: I marked the part it checked the Adobe version.
Well shortly the shellcode will look like below, contains the payload's url:
*) Noted: I marked the part it checked the Adobe version.
Well shortly the shellcode will look like below, contains the payload's url:
 Well, I just downloaded it..
Well, I just downloaded it..
GET /closest/209tuj2dsljdglsgjwrigslgkjskga.php?rjh=30:1n:%201i:1i:33&ofa=30:33:1n:1m:1h:33:30:1o:30:1h&omtvgame=1i&tdn=trnwuek&hxx=ynkt HTTP/1.0
Referer: http://malwaremustdie.blogspot.com
User-Agent: Gottcha!
Host: 33sdfguuh.mywww.biz
:
HTTP request sent, awaiting response...
HTTP/1.1 200 OK
Server: nginx/1.2.6
Date: Tue, 05 Feb 2013 13:17:33 GMT
Content-Type: application/x-msdownload
Content-Length: 176128
Connection: keep-alive
X-Powered-By: PHP/5.3.10-1ubuntu3.4
Pragma: public
Expires: Tue, 05 Feb 2013 13:17:40 GMT
Cache-Control: must-revalidate, post-check=0, pre-check=0
Cache-Control: private
Content-Disposition: attachment; filename="contacts.exe"
Content-Transfer-Encoding: binary
:
200 OK
Registered socket 1892 for persistent reuse.
Length: 176128 (172K) [application/x-msdownload]
Saving to: `contacts.exe'
2013-02-05 22:17:37 (84.9 KB/s) - `contacts.exe' saved [176128/176128]
Now we have the payload below:
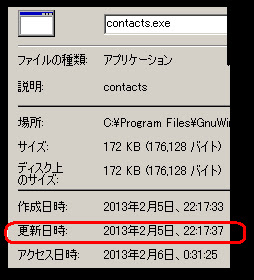 *)Noted: I marked my local time of my PC when I fetched.
Nothing special about the file's looks & dull-usual name of contacts.exe
*)Noted: I marked my local time of my PC when I fetched.
Nothing special about the file's looks & dull-usual name of contacts.exe
Debug investigation of the payload
So it's time to debug it to understand:
1. First the moronz encrypted the binary, see -->>[HERE]
the section .text and .data was garbled,
trailing the bins made me only stuck at the 0x40A209 in .text section:
0x40A209 add esi, 1Fh
0x40A20C pushf
0x40A20D or word ptr [esp], 1
0x40A212 nop
0x40A213 popf
0x40A214 wait
0x40A215 push ebp
0x40A216 wait
0x40A217 pop ebp
0x40A218 nop
0x40A219 rep cld
0x40A21B jb loc_40A49D
0x40A221 pop ds
0x40A222 pop ds
0x40A223 cmp dl, bh
0x40A225 push ecx
: (skip)
0x40A229 var_44 = word ptr -6583D684h
0x40A229 var_42 = byte ptr -6583D682h
0x40A229 var_25 = byte ptr -6583D665h
0x40A229 var_23 = byte ptr -6583D663h
: (skip)
0x40A2F9 ; FUNCTION CHUNK AT 0x40A6EF
0x40A2F9 ; FUNCTION CHUNK AT 0x40A839
0x40A2F9 ; FUNCTION CHUNK AT 0x40A874
: (skip)
0x40A2F9 ; FUNCTION CHUNK AT 0x40FC08
0x40A2F9 ; FUNCTION CHUNK AT 0x40FC63
2. Shortly I figured some mistery by debugging it to find these clue:
This mess loading DLL by using these methods..
LdrLoadDll
LdrGetDllHandle
Use below command to decrypt:
uncrypted.exe
Microsoft Base Cryptographic Provider v1.0
Detecting/search the below programs / services:
Windows Defender
wscntfy.exe
MSASCui.exe
MpCmdRun.exe
NisSrv.exe
msseces.exe
fp.exe
:
MsMpSvc
windefend
SharedAccess
iphlpsvc
wscsvc
mpssvc
Debugged further to find that this malware stopping these processes:
MsMpSvc, windefen, SharedAccess, iphlpsvc, wscsvc, mpssvc, bfe
PoC code in ASM here -->>[PASTEBIN]
Looks also erasing/throwing off something via registry:
RECYCLER\
$Recycle.Bin\
With some more registry traces...
InprocServer32
{fbeb8a05-beee-4442-804e-409d6c4515e9}
\registry\machine\Software\Classes\clsid\{5839fca9-774d-42a1-acda-d6a79037f57f}\InprocServer32
:
A nice attempt to use his filename to save itself..
TEMP=
\InstallFlashPlayer.exe
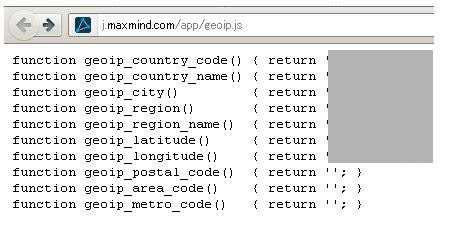
Internet access command -1- Get GeoIP Info & safe/get CN code..
GET /app/geoip.js HTTP/1.0
Host: j.maxmind.com
Connection: close
:
geoip_country_code
If you simulate this into your browser, you'll get
your all GeoIP data + lat/long coordinates.
 Internet access command -2- get the counter...
Internet access command -2- get the counter...
GET /5699017-3C912481A04E584CDF231C519E1DF857/counter.img?theme=%u&digits=10&siteId=%u HTTP/1.1
Host: bigfatcounters.com
User-Agent: Opera/9 (Windows NT %u.%u; %s; %s)
Connection: close
I dumped this data from memory after fetching the last URL above...
 ↑oh.. is an image file.. a counter↓
↑oh.. is an image file.. a counter↓

Behavior Analysis
So what was happened when I run it? It was as per below snapshot:
 The execution of CMD for self (copy+)deletion..
It requests the DNS query to the google, AND to these specific IP!↓
The execution of CMD for self (copy+)deletion..
It requests the DNS query to the google, AND to these specific IP!↓
194.165.17.3:53 ADM-SERVICE-NET (Monaco)
66.85.130.234:53 TechEVE Ltd TE-SAFESUGAR (UK)
Except the above http, I detected UDP request to access these IP/port:
92.254.253.254:16464
88.254.253.254:16464
87.254.253.254:16464
71.254.253.254:16464
69.254.253.254:16464
1.172.141.253:16464
122.110.95.253:16464
85.86.69.253:16464
90.230.2.2:16464
115.31.23.2:16464
174.101.87.249:16464
187.74.74.249:16464
61.86.42.249:16464
194.165.17.3:123
91.242.217.247:123
94.183.234.248:16464
180.254.253.254:16464
166.254.253.254:16464
135.254.253.254:16464
134.254.253.254:16464
119.254.253.254:16464
117.254.253.254:16464
115.254.253.254:16464
126.13.87.248:16464
89.215.205.2:16464
222.109.23.4:16464
203.171.244.4:16464
109.90.149.240:16464
173.217.73.3:16464
98.26.183.2:16464
84.55.11.24:16464
116.73.35.4:16464
86.126.1.74:16464
121.242.162.55:16464
175.181.230.42:16464
190.208.75.36:16464
150.214.68.251:16464
188.6.88.61:16464
206.254.253.254:16464
190.254.253.254:16464
182.254.253.254:16464
A short session of infection goes like this:
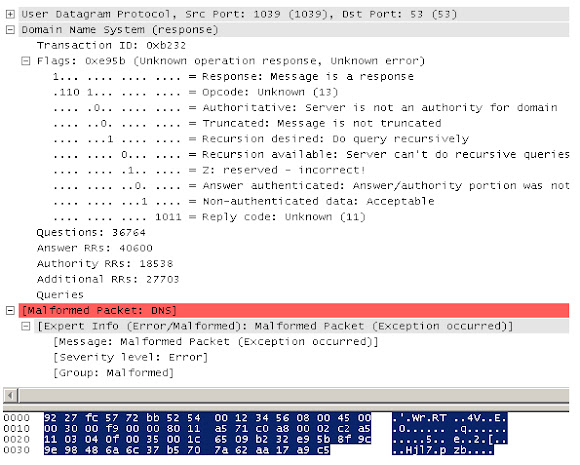
 And these are the snapshot of UDP, malform DNS requests I was talking about:
And these are the snapshot of UDP, malform DNS requests I was talking about:
 It sent the malform DNS with the request is like this:
It sent the malform DNS with the request is like this:
 Any idea what is this, friends? :-)
Furthermore let's see what's the file process & networking + registry-->>[HERE]
Is a full run log on asession of one infection I made it on my PC :-)
Please try to grep values like "RegSet" or "CreateFile", "UDP" to be more focus
in understanding how this malware's work.
In registry there's some changes in:
Any idea what is this, friends? :-)
Furthermore let's see what's the file process & networking + registry-->>[HERE]
Is a full run log on asession of one infection I made it on my PC :-)
Please try to grep values like "RegSet" or "CreateFile", "UDP" to be more focus
in understanding how this malware's work.
In registry there's some changes in:
HKLM\Software\Classes\ClsId\{...some ID....}\InprocServer32\
--→"C:\WINDOWS\system32\wbem\fastprox.dll"/"C:\RECYCLER\S-1-5-18\$6576a1a85f9fdb0e20568660563a58ee\n."
↑wow, looks like a setup for a deletion ...
Noticing the above, I just realized that my below registry keys were deleted/gone..
..\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy
..\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile
..\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile\AuthorizedApplications
..\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile\AuthorizedApplications\List
..\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile
..\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications
..\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
..\System\CurrentControlSet\Services\SharedAccess\Setup
..\System\CurrentControlSet\Services\SharedAccess\Setup\InterfacesUnfirewalledAtUpdate
..\System\CurrentControlSet\Services\wscsvc
..\System\CurrentControlSet\Services\wscsvc\Enum
..\System\CurrentControlSet\Services\wscsvc\Parameters
..\System\CurrentControlSet\Services\wscsvc\Security
Now I know why it seeked those strings of programs in debugging, to DELETE them..
Moreover saw an a fail attempt of starting the Active Directory Domain Services Database
Mounting Tool or SERVICES_ACTIVE_DATABASE, binding to the localhost...
What's this mess?
So we are dealing with what malware then? 1) a trojan (for sure, by all infection
MO & erasing stuffs) + staring service, but for what?
I wonder what would happened if one of those request to had seccessfully established.
IF it sent data then we have 2) a spyware which is having these characteristics.
Let's reseacrh further, viewing the way it made changes in registry at the
recycle keys/values made made me bumped to the good writing about ZeroAccess Recycler
version here -->>[TigzyBlog]
And UDP/16464 found it as the ZeroAccess/alias MaxPlus, Sirefef variant.
Thank's to the Tigzy-RK for a useful writing -->Tigzy-RK
And all of the advices I received, I thank you.
Samples
Here's the overall samples -->>[HERE]
(Samples are shared for raising detection ratio & research purpose)
*) Thank you to @Horgh_rce for adding the unpack version of the malware.
It's really good to know that I didn't miss a thing during debugging.
Virus Total
Below is detection ratio as per detected moment of the samples in VT:
Landing page : (1/46) -->
>[VT]
PDF1 : (20/46) -->
>[VT]
PDF2 : (13/46) -->
>[VT]
JAR1 : (6/46) -->
>[VT]
JAR2 : (5/46) -->
>[VT]
Payload : (6/46) -->
>[VT]The Infection
I don't have time to check these all but all of these BHEK are infecting
same ZeroAccess variant now. Marked the domain name & BHEK "/closest" path:
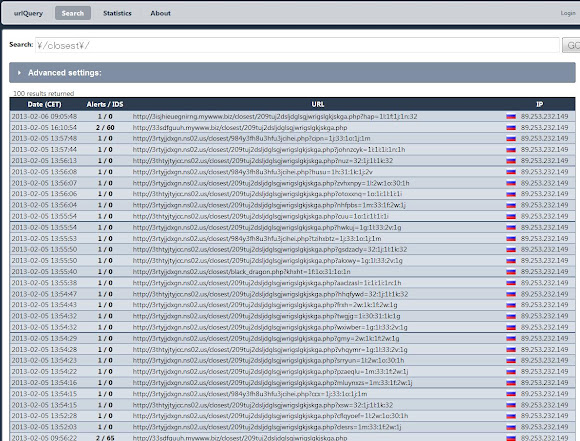 The PoC of the list in the picture above is --->>[HERE] and here -->>[HERE]
The PoC of the list in the picture above is --->>[HERE] and here -->>[HERE]
Thank you for your help, advice & cooperation!
#MalwareMustDie!
FYI the 2 PDFs urls is are as per below (this is for people who got attack by these Blackhole which mostly seeing these PDF downloads URL in their log..)
h00p://33sdfguuh.mywww.biz/closest/209tuj2dsljdglsgjwrigslgkjskga.php?dsmq=30:1n:1i:1i:33&lllsxi=3g:3a:3c&bdm=30:33:1n:1m:1h:33:30:1o:30:1h&uzz=1k:1d:1f:1d:1g:1d:1f h00p://33sdfguuh.mywww.biz/closest/209tuj2dsljdglsgjwrigslgkjskga.php?qbzntsus=30:1n:1i:1i:33&cazv=39&alltb=30:33:1n:1m:1h:33:30:1o:30:1h&mkitrggt=1k:1d:1f:1d:1g:1d:1fI started to get the payload from the smallest size of PDF, to find the JS/Evil/Code written in the 0x11AF-0x2768 section with text below:The red mark is the evil script, where the purple mark is the long obfuscation var/array, and the yellow mark is the deobfuscator logic. Following the usual method to decode this, we'll find the infector script burped as per first upper part below, marked area is the shellcode in text:
And the lower part which having Libtiff overflow CVE-2010-0188 exploit code:
*) Noted: I marked the part it checked the Adobe version. Well shortly the shellcode will look like below, contains the payload's url:
Well, I just downloaded it..
GET /closest/209tuj2dsljdglsgjwrigslgkjskga.php?rjh=30:1n:%201i:1i:33&ofa=30:33:1n:1m:1h:33:30:1o:30:1h&omtvgame=1i&tdn=trnwuek&hxx=ynkt HTTP/1.0 Referer: http://malwaremustdie.blogspot.com User-Agent: Gottcha! Host: 33sdfguuh.mywww.biz : HTTP request sent, awaiting response... HTTP/1.1 200 OK Server: nginx/1.2.6 Date: Tue, 05 Feb 2013 13:17:33 GMT Content-Type: application/x-msdownload Content-Length: 176128 Connection: keep-alive X-Powered-By: PHP/5.3.10-1ubuntu3.4 Pragma: public Expires: Tue, 05 Feb 2013 13:17:40 GMT Cache-Control: must-revalidate, post-check=0, pre-check=0 Cache-Control: private Content-Disposition: attachment; filename="contacts.exe" Content-Transfer-Encoding: binary : 200 OK Registered socket 1892 for persistent reuse. Length: 176128 (172K) [application/x-msdownload] Saving to: `contacts.exe' 2013-02-05 22:17:37 (84.9 KB/s) - `contacts.exe' saved [176128/176128]Now we have the payload below:*)Noted: I marked my local time of my PC when I fetched. Nothing special about the file's looks & dull-usual name of contacts.exe
Internet access command -2- get the counter...
GET /5699017-3C912481A04E584CDF231C519E1DF857/counter.img?theme=%u&digits=10&siteId=%u HTTP/1.1 Host: bigfatcounters.com User-Agent: Opera/9 (Windows NT %u.%u; %s; %s) Connection: closeI dumped this data from memory after fetching the last URL above...↑oh.. is an image file.. a counter↓

The execution of CMD for self (copy+)deletion.. It requests the DNS query to the google, AND to these specific IP!↓
194.165.17.3:53 ADM-SERVICE-NET (Monaco) 66.85.130.234:53 TechEVE Ltd TE-SAFESUGAR (UK)Except the above http, I detected UDP request to access these IP/port:92.254.253.254:16464 88.254.253.254:16464 87.254.253.254:16464 71.254.253.254:16464 69.254.253.254:16464 1.172.141.253:16464 122.110.95.253:16464 85.86.69.253:16464 90.230.2.2:16464 115.31.23.2:16464 174.101.87.249:16464 187.74.74.249:16464 61.86.42.249:16464 194.165.17.3:123 91.242.217.247:123 94.183.234.248:16464 180.254.253.254:16464 166.254.253.254:16464 135.254.253.254:16464 134.254.253.254:16464 119.254.253.254:16464 117.254.253.254:16464 115.254.253.254:16464 126.13.87.248:16464 89.215.205.2:16464 222.109.23.4:16464 203.171.244.4:16464 109.90.149.240:16464 173.217.73.3:16464 98.26.183.2:16464 84.55.11.24:16464 116.73.35.4:16464 86.126.1.74:16464 121.242.162.55:16464 175.181.230.42:16464 190.208.75.36:16464 150.214.68.251:16464 188.6.88.61:16464 206.254.253.254:16464 190.254.253.254:16464 182.254.253.254:16464A short session of infection goes like this:And these are the snapshot of UDP, malform DNS requests I was talking about:
It sent the malform DNS with the request is like this:
Any idea what is this, friends? :-) Furthermore let's see what's the file process & networking + registry-->>[HERE] Is a full run log on asession of one infection I made it on my PC :-) Please try to grep values like "RegSet" or "CreateFile", "UDP" to be more focus in understanding how this malware's work. In registry there's some changes in:
The PoC of the list in the picture above is --->>[HERE] and here -->>[HERE]